Copy Protection
Introduction
This page describes the copy protection schemes implemented on all platforms that Dungeon Master and/or Chaos Strikes Back were released on.
The earlier versions released on Atari ST, Amiga and Apple IIGS feature very sophisticated copy protection schemes. Other versions have much weaker protections and some of them have no copy protection at all (check the Platform-specific details section).
It took several months after the first release of Dungeon Master on Atari ST before the copy protection was fully defeated, while most copy protections are defeated in a matter of hours or days by experienced hackers. This partially explains why they sold lots of copies, the main reason being, of course, that this is a great game!
An expert hacker speaks
Read what Andy The Arfling (a hacker once member of the BBC / Automation groups) said about the Dungeon Master copy protection in an Interview of a hacker talking about the Dungeon Master copy protection:
What’s the best protection system you have ever seen?
Encryption routines were a silly game, so the best protection has to be Dungeon Master as far as I’m concerned. Law has mentioned a decryption routine I wrote running on the keyboard processor, but it was still beaten by hardware.
What’s the best job of a game crack (ST) you have ever seen?
Dungeon Master. It seemed to be written in some kind of interpreted language which made it very difficult to fathom. It also had protection embedded throughout the game. Good protection is like good encryption, it can never be an afterthought, you can’t buy it off the shelf, it has to be part of the fabric of the game. Apparently it had a protection check after the final boss, just so you couldn’t see the end sequence. Hats off to them. Hats off to Was (Not Was) for cracking it.
Message posted by Doug Bell about the copy protection
Doug Bell was the main programmer of Dungeon Master and its copy protection.
Posted on 06/09/2008 at 16:55 on http://www.next-gen.biz/index.php?option=com_content&task=view&id=10800&Itemid=50&show=1&start=8 (link is now dead)
Of course it is a difficult question to say how much more or less revenue a product would have earned with or without copy protection. The answer to the question is dependent on a number of factors including the effectiveness of the copy protection and availability of similar products at different price points with and without effective copy protection.
There are at least four different interest groups, with the lines between them blurred at times:
1) Software developers and publishers seeking to maximize the return on their efforts;
2) Paying customers interested in receiving value in exchange for their money;
3) Pirates interested in using the software while illegally minimizing or eliminating costs; and
4) Crackers interested in the technical challenge, notoriety and/or financial gain from circumventing the technical barriers to copying or pirating the software.
Each interest group offers up their own reasons and rationales to justify their actions. Crackers argue the copy protection is pointless because it can always be circumvented as if this somehow bestows their activities with some form of populist nobility. Pirates argue that they wouldn’t have paid for the product anyway, so their actions somehow don’t really amount to stealing from the developer. Paying customers are frustrated by paying for a product that is less functional or more cumbersome to use than the stolen version used by the pirate. Finally, the resources available to software developers to invest in creating software are limited by the revenue they earn and reduced by the resources invested in copy protection. All in all, this creates a tough situation to analyze.
However, as the developer of a must-have computer game (albeit from a couple of decades ago) that you had to actually buy, I may have the rare perspective to take a stab at the question. Back in 1988, cartridge games were rarely pirated while computer games were rampantly pirated. Most games were cracked within a week of being released, with probably significantly less than 1% of software remaining uncracked after two weeks. One notable exception during this period was the game Dungeon Master, which was the best selling game on several different personal computer platforms over a two-year period. Dungeon Master was first released on the Atari ST, and for the better part of a year the only way to play Dungeon Master was to own an Atari ST and to buy the game.
Dungeon Master exposed the fallacy in the claims of both the pirates and the crackers. The pirates who would never have paid for the game if they could steal it did pay for it. Despite a steadily growing bounty of fame and notoriety for cracking the game, the protection lasted more than a year. And the paying customer was rewarded with not just a minimally invasive copy protection scheme, but just as importantly, with the satisfaction of not feeling like a schmuck for paying for something that most people were stealing.
As the developer of both Dungeon Master and the software portion of its copy protection, I knew that eventually the copy protection would be broken, but that the longer it held out the less damage we would suffer when it was broken. We had the advantage of owning the patent on a floppy-disk copy protection scheme that required a $40,000 specialized hardware device to write the disks. It was impossible to create a disk image without this hardware, and the hardware itself was out of production. That meant that as long as there were enough layers on the copy protection, and these layers took long enough to crack, the only way to own the game was to buy it. The copy protection scheme took a couple of weeks to create, and while this added cost to the production without adding value for the customer, it was time well spent. The copy protection was based on many redundant, overlapping and isolated checks and cross checks. The copy protection was developed with the assumption that the cracker would be armed with a hardware emulator and developed with an awareness of the capabilities and limitations of the commonly available emulators of the time.
*Dungeon Master had a greater than 50% market penetration on the Atari ST—that is, more than one copy of Dungeon Master was sold for each two Atari ST computers sold. That’s easily 10 times the penetration of any other game of the time on any other platform. *
So what’s the lesson? That piracy does take significant money out the pocket of the developer and that secure anti-piracy schemes are viable.
Magazine article
- Dragon Magazine (United Kingdom-USA)
 Dungeon Master Copy Protection (Atari ST) ArticleDragon Magazine (United Kingdom-USA), Issue No 200 Vol XVIII No 7 December 1993, Page 73[Credits: Internet Archive]
Dungeon Master Copy Protection (Atari ST) ArticleDragon Magazine (United Kingdom-USA), Issue No 200 Vol XVIII No 7 December 1993, Page 73[Credits: Internet Archive]
Overview
Principle
Copy protected floppy disks require two things:
- The use of special hardware and/or software to write something unusual on the floppy disk: an anomaly, a deliberate inconsistency, something that does not fully respect the standard way to store data on a floppy disk. It is important that this unusual thing can be detected by the hardware and software available on the computer of the player, and it is also important that this unusual thing cannot be written to a another floppy disk using the consumer grade hardware and software tools available on the player’s computer, which all have some limitations in their capabilities. This ensures that the original floppy disk can only be duplicated with the special hardware/software and not on regular computers using common disk copy tools.
- A program that will check for the presence of the unusual thing on the floppy disk. If present, the game will play normally. If missing, the game detects that it is running from an illegitimate copy and may react accordingly. Game play may stop immediately or the game experience may degrade over time with no explicit reasons.
Pirates want to be able to copy the floppy disks easily, and because they cannot circumvent the hardware limitations of the home computers, their only solution is to change the original program to disable the copy protection checks. The job of crackers is to analyze the program to find the copy protection checks and neutralize them, for example by replacing some instructions to bypass them.
The next sections will show the smart ideas that FTL used to make the life of crackers as hard as possible.
Preventing floppy disk copy
Several techniques were used to place “unusual things” on the original floppy disks of Dungeon Master and Chaos Strikes Back to prevent easy disk copy. Check the ‘Platform-specific details’ section for more information.
The main technique is the use of “fuzzy bits”, also known as “weak bits” or “flakey bits” as they are called at the Software Preservation Society (SPS, ex CAPS). The main characteristic of fuzzy bits is that sometimes their value reads as ‘0’ and sometimes it reads as ‘1’: it is random.
There are several ways to create fuzzy bits:
- The method used on Atari ST, Amiga and Apple IIGS relies on placing magnetic flux reversals at ambiguous timings. It is described in detail on Detailed analysis of Atari ST Floppy Disks of Dungeon Master and Chaos Strikes Back and Copy Protection of Dungeon Master for Apple IIGS. That method was invented by Kevin R. Kachikian when he was working for a company named ‘First Byte’ which filed a patent application. Software Heaven, Inc. (FTL Games’ parent company) acquired it when First Byte went out of business. The patent was later granted to Software Heaven, Inc. As described and photographed in an FTL Article published in German magazine ‘Power Play’, April 1988, Page 83, FTL Games used its own disk duplication machine manufactured by ‘Formaster’ (which would later become ‘Trace’) to produce their floppy disks. Check the US Patent #4849836 ‘Copy protection for computer discs’ on Google Patent Search.
It is NOT possible to write such fuzzy bits on a floppy disk by using standard hardware like the floppy disk drives and controllers found in personal computers like Atari ST, Amiga, PC, Macintosh, etc… Specialized hardware is required and this was very expensive back at the time (more than buying the game). - The method used on Japanese platforms X68000 and PC-9801 is different and relies on a ’no flux area’: an area without any magnetic flux reversals that is longer than the maximum allowed by the specifications. If too many 0 bits (no flux reversals) are written one after the other then this is a violation of the encoding rules (too many means more than three in MFM or more than 2 in GCR 6 and 2). When reading this ’no flux area’, the floppy disk controller (FDC) detects that no flux reversal occurred in the expected timeframe and this triggers the AGC (Automatic Gain Control) to increase the amplification of the analog signal coming from the floppy disk drive, up to the point that noise signal will get large enough to cause a reversal, causing the output of fake random ‘1’ bits.
This kind of no flux area cannot be created on most computers (including Atari ST and PC) because their FDC enforces the encoding rules, but it can be created with an Amiga.
Detecting non-original disks
In order to check if the floppy disk is original, the game reads the fuzzy bits several times and compares the results: if their value is different from one reading to another then the disk is an original. If their value is always the same then the disk is a copy.
Dungeon Master reads the copy protection sector containing the fuzzy bits periodically during gameplay: when starting a game and when moving to another level (only if the previous reading did not occur too recently). The detection of a single bit with changing value is enough for the program to consider the disk as original.
The copy protection code in the Atari ST/Amiga/Apple IIGS versions checks that at least some of the fuzzy bits have random values but it also checks that all the other bits in the sector are not random. This is important because creating random bits can be achieved in another way (the one used on X68000 and PC-9801), at least on Amiga (but not on Atari ST), and it requires writing a series of ‘0’ bits.
If the copy protection was only looking for any random bits in the sector, it would be possible to copy the game on Amiga using a special purpose program. The way the fuzzy bits were actually created on Atari ST/Amiga/Apple IIGS ensures that special hardware is required to provide the ability to position reversals with very accurate (and ambiguous) timings, something that was not possible on any consumer-grade hardware available when the games were released.
Preventing software crack
Cracking a program means modifying the program so that it will bypass its copy protection check. In the case of Dungeon Master, that means removing or bypassing the test that checks for the presence of fuzzy bits.
The designers knew that software pirates would try to crack their games so they included a lot of tricks to make their task as difficult as possible.
Multiple checks
Many copy protection checks involve a single test when the game starts. It is relatively easy for pirates to find and remove such tests.
In the case of Dungeon Master and Chaos Strikes Back, the developers put several checks for the presence of fuzzy bits at various places in the program. For a “good” crack, you need to find and defeat them all.
Hidden code in GRAPHICS.DAT
In order to make things even harder, the designers put some hidden code pieces in the graphics.dat file. These routines are encoded just like normal images. At some points while you play, these hidden code pieces are decoded in memory, executed and then cleaned from memory. A pirate looking only at the main program would miss them.
You can see these routines disassembled on Dungeon Master and Chaos Strikes Back Graphics.dat: Hidden code.
Checksums
A checksum is a computed value which depends on the contents of a block of data. Their main characteristic is that if you change anything in the data, then the checksum value will also change.
Dungeon Master uses checksums at several places in the program to ensure that the program itself has not been tampered with. If a pirate changes something in the code to remove one part of the copy protection, then the program is changed. The checksum of the program also changes so the program can itself detect the change and know that it has been cracked. Ultimately, it will also break and prevent you from playing the game normally.
That makes the cracking task harder, because you need to find and neutralize all these checksums, in addition to the other disk validation tests.
Delayed results to failed tests
In many games, the copy protection checks immediately return an error message when a copy is detected. Some copy protection checks work in that way in Dungeon Master. But it is also more vicious: when some of the multiple copy protection tests fail, the game will often not stop immediately. Instead you will be able to keep playing for several minutes (or even hours in certain cases). But ultimately, you will face the consequences in one way or another (see below). The fact that a pirate cannot immediately know if the crack he made is working fine in the long term requires lots of testing and time, and very careful inspection of what the program is doing. This makes the cracking process a lot harder and longer.
Various results to failed tests
If the game detects a copied disk or that the program was modified then it can produce different effects, immediate or delayed:
- The game hangs, crashes or deliberately runs out of memory.
- The game displays a dialog box with the message “THAT’S NOT THE MASTER DISK!”
- When clicking on the disk icon, the champion inventory is closed instead of opening the save menu.
- Mouse clicks are ignored.
- Animation stops (thrown items remain in the air, door do not open/close, creatures do not move, etc.). Soon after this the following message is displayed: “SYSTEM ERROR 60”.
- Altars of Vi cannot be used anymore
- Instant death of the whole party. When this happens, you do not have the option to “Restart this game” as you usually have when your party is killed during combat.
Copy protection issues
Although very sophisticated, that copy protection scheme has some drawbacks:
- Installation on hard disk is not possible (note that there are tools and hacked versions that can run the games from a hard drive).
- On Amiga, the copy protection is responsible for compatibility issues with some newer kickstart versions and some faster processors like 68030. That is probably one of the reasons why they removed the protection in the latest Psygnosis release (version 3.6). Note that even without the copy protection, this version still cannot be installed on hard disk directly because the name of the floppy disk is hard coded in the program to open data files.
Platform-specific details
Atari ST
See Detailed analysis of Atari ST Floppy Disks of Dungeon Master and Chaos Strikes Back
If you want to study the software side of the copy protection, you may download ReDMCSB here. It contains the source code of the Atari ST versions and a detailed documentation of the copy protection schemes in these versions.
Boot sequence
In Atari ST versions, a custom floppy disk boot sector runs SWOOSH.IMG. This program displays the FTL logo and plays the associated sound. Then it runs START.PRG which is a small program that decompresses in memory the main program stored in START.PAK. The main program is then run in memory.
START.PRG is run with the “AUTO” command line parameter which is forwarded to the main program in START.PAK. That is another protection: you cannot run the program directly if you copied the files to your hard disk.
How to detect an original or a copy?
On an Atari ST with 1 MB of memory (so that all the game fits in memory), you can detect if the game is an original. If there are short disk accesses while playing (mostly when changing levels), that means the copy protection is probably still there. If you can play for several hours then you have an original.
You may be able to finish Dungeon Master even with a copied version if you save often. Chaos Strikes Back breaks faster than Dungeon Master because there are a lot more level changes.
Commodore Amiga
Amiga uses 3.5" floppy disks with a rotation speed of 300 rpm and use the MFM encoding.
The storage capacity is: 2 sides x 80 tracks x 11 sectors per track x 512 bytes per sector = 901120 Bytes = 880 KB.
Amiga tracks can store more data than other format because the Amiga always writes full tracks, not individual sectors. The benefit is that all gaps between sectors are reduced compared to other formats, which increases the useful storage.
The copy protection on Amiga is very similar to the Atari ST one. The sector 247 found on the Atari ST disk is not present, however the sector that contains fuzzy bits is also present on the Amiga versions of Dungeon Master and Chaos Strikes Back (only on the game disk, not on the Chaos Strikes Back Utility Disk). Track 0 on side 1 is formatted as a 10 sectors Atari ST track just like all tracks on the Atari ST floppy disks (and not an Amiga track like all other tracks on the Amiga floppy disk). The copy protection sector is sector 1 for Dungeon Master 2.x versions and it is sector 2 for Chaos Strikes Back versions 3.x. Other sectors in the track are regular sectors, they are not used by the copy protection and filled with $E5 bytes.
Dungeon Master Demo version 2.0 and Dungeon Master 3.6 are not copy protected and this Atari ST track is not present.
Boot sequence
Dungeon Master for Amiga version 2.x:
Unlike the Atari ST versions, the game is not run from the boot block but uses the standard startup-sequence script located in the folder “s” on the disk. This script runs a loader called “exec”. This loader sets up a few things like display and memory reservations.
This program is “self detaching”, which means that it detaches itself from the process that launched it. In fact, it creates a new process for itself and then terminates. In later versions (like in Chaos Strikes Back for Amiga version 3.1), the loader is called “bjeload_r” and does the same thing. It can be seen if you run it in a shell: the program seems to terminate immediately without doing anything, then the game starts.
The loader runs the “swoosh” program (displaying the FTL logo and playing the associated sound), and then the main program “dm”. In fact, it runs “DungeonMaster:swoosh” and then “DungeonMaster:dm” because it refers to the floppy disk by its name. That is why you need to assign the name of the floppy disk to a hard disk folder if you want to play from hard disk (with a hacked version as the original does not permit this).
Apple IIGS
See Copy Protection of Dungeon Master for Apple IIGS
Sharp X68000
Floppy disks for Japanese computers (X68000, PC-9801 and FM-Towns) all use the same format for both 5.25 inch and 3.5 inch floppy disks. They all have a rotation speed of 360 rpm and use the MFM encoding.
The storage capacity is: 2 sides x 77 tracks x 8 sectors per track x 1024 bytes per sector = 1261568 Bytes = 1232 KB.
The information and screenshots below results from the analysis of Kryoflux raw images of these floppy disks with the ‘Track Analyzer’ feature that is part of the HxC Floppy Emulator.
Dungeon Master and Chaos Strikes Back for X68000 both use exactly the same copy protection, which is much weaker than the copy protection found in the Atari ST/Amiga/Apple IIGS versions.
There are several clues showing that the copy protection implementation was incomplete and/or rushed:
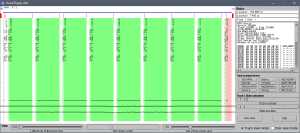
- Non standard features of the floppy disk format designed to prevent copying with standard hardware but whose presence is not checked by the program: on Track 1 Side 0 there are fake sectors 245, 246 and 247 that overlap some of the regular sectors. They appear in red on this screenshot:
Note that sector 1 is ‘inside’ both sectors 245 and 246 which both end in the middle of sector 2. Sector 247 starts between sectors 4 and 5 and ends in the middle of sector 6. - Many copy protection schemes that are part of the Atari ST/Amiga/Apple IIGS versions are still present in the code but they are deliberately disabled.
- One of the only two remaining copy protection schemes is broken: a software bug makes it completely ineffective at detecting a non-original floppy disk.
Compared to Dungeon Master for X68000, Chaos Strikes Back for X68000 contains code for an additional consequence of a failed copy protection check (to prevent saving the game), however the bug also makes it ineffective.
There is only one copy protection scheme that is still operational:
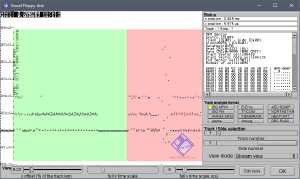
Track 1 on side 1 contains a sector 0 with no data (on the left of the screenshot) and a fake sector 9 (in addition to the regular 8 sectors) as shown in red at the right of this screenshot:
This sector contains only a few useful bytes of data: the string ‘HPR-0007’ followed by 4 bytes that give random values each time they are read (visible in the rightmost part of the screenshot).
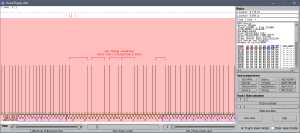
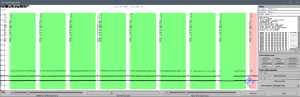
This animation shows the randomness of these 4 bytes:- In the middle of the red area, the timings between flux reversals are visible for several rotations of the same disk. There are great variations in this area which corresponds to the 4 random bytes. This proves that this area does not contain any actual flux reversals (otherwise they would be found with approximately the same timing in each rotation, just like the timings of all other flux reversals). The FDC always expects to detect flux reversals at the standard MFM timing intervals. When no reversals are detected, the AGC (Automatic Gain Control) amplifies the analog signal coming from the floppy disk drive until a fake reversal is detected, which is only caused by amplified noise in this case. This explains why the reversals are not detected at the same locations on each rotation of the disk.
- On the right part, the decoded sector content is displayed: the ‘HPR-0007’ string followed by 4 bytes with random values. The following byte values may also seem random as their values also change in the animation, however this is only a side effect of the previous 4 random bytes. Actually these correspond to regular flux reversals on the disk and only reflect that MFM decoding is desynchronized after reading the random bytes, depending on their value. Synchronization gets fine again after reading the synchronization marks preceding the next sector so this desynchronization does not create any issue. After the 4 random bytes, MFM decoding may start anywhere, on a clock or data bit and not necessarily on a byte boundary. However all the observed byte values correspond to the very same MFM bit stream (consisting of alternating data bits and clock bits), it only depends on which bit the decoding starts at:
79 79 79 BC BC BC 5E 5E 5E 2F 2F 2F 97 97 97 CB CB CB E5 E5 E5 <- Actual data written on the disk 72 F2 F2 <- The first byte may not have the Data bits 0 1 1 1 0 0 1 0 1 1 1 1 0 0 1 0 1 1 1 1 0 0 1 0 1 1 1 1 0 0 1 same value as the Clock bits 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 0 0 0 0 0 1 0 0 next ones depending 08 08 08 on the value of the 10 10 10 preceding random bit 20 20 20 40 40 40 80 80 80 01 01 01 02 02 02 04 04 04
The following annotated screenshot shows the MFM timing violations in the 4 random bytes area:
Each time the program checks for the presence of the game disk in the drive (including at the very beginning when starting or loading a game), it reads this fake sector 9 twice and makes sure that the resulting byte values are different. If they both give the same result then the program displays a message requesting insertion of the game disk until an original disk is detected.
Other weaknesses:
- No delayed consequences after failed copy protection checks (there would be some if the second copy protection scheme was not broken). When the copy protection check fails, the consequence is immediate so it is fairly easy for a hacker to analyze what the program is doing at this time.
- Limited checksum of program code to detect tampering: only a simple sum of bytes is used. In Atari ST, Amiga and Apple IIGS there are multiple checksum algorithms applied to check the code of the most important copy protection functions. Any modification of these functions results in at least one checksum error, allowing the game to detect cracking attempts.
Dungeon Master for X68000 was cracked by modifying a function in a way that does not change the checksum value (see Dungeon Master for X68000). The same crack would be applicable to Chaos Strikes Back if the program was not compressed. Note that even if the crack did change the checksum result, disabling the checksum test would also be fairly simple (changing only one byte in DM.X). A similar crack would be required for the Champion Editor that contains very similar code. - Another weakness lies in the way the copy protection sector is read. On Atari ST, Amiga and Apple IIGS, there are custom routines in the game that directly manipulate the floppy disk controller chip to read the copy protection sector. Bypassing these routines requires modifications of the program code which would trigger the checksum errors. On X68000 on the other hand, all read operations of the copy protection sector are performed using the native IOCS operating system routine named B_READ. Chaos Strikes Back was cracked with a program that intercepts and bypasses calls to this native OS routine, and this crack also works with Dungeon Master. With this method, there is no need to modify any of the original files so that checksums remain valid. Before starting the game, the small program called CK.R is installed in memory to intercept all calls to B_READ. If a call is made to read the copy protection sector, the program returns what is expected by the game, just as if it had really been read from the floppy disk. Otherwise, it calls the real B_READ routine and lets it do its regular job. CK.R is found in the floppy disk image available for download at Chaos Strikes Back for X68000.
Here is the assembly source code of CK.R:clr.l -(sp) dc.w $FF20 ; DOS call SUPER() addq.l #4,sp lea Routine,a0 lea ($F00).l,a1 ; Address of unused memory ; in the IOCS work area ; $000800 - $001000 ; Crack routine is copied there movea.l a1,a2 move.w #$10,d0 ; Loop to copy the routine copy_loop: move.l (a0)+,(a1)+ dbf d0,copy_loop lea ($518).l,a0 ; Get original B_READ ($46) routine address ; $518 = $400 (base) + 4 * $46 move.l (a0),d0 move.l d0,$3A(a2) ; Copy original routine address in jmp instruction move.l a2,(a0) ; Replace the Read Sector routine dc.w $FF00 ; DOS call EXIT() Routine: cmp.w #$9000,d1 bcs.s Call_B_READ ; Branch if call is not for first floppy drive ; (value between $9000 and $9100) cmp.w #$9100,d1 bcc.s Call_B_READ cmp.l #$1010109,d2 bne.s Call_B_READ ; If not reading copy protection sector movem.l a0-a1,-(sp) ; Write bytes expected by the game: ; 'HPR-0007' string ; Followed by 4 random bytes (here a simple counter) move.l #'HPR-',(a1)+ move.l #'0007',(a1)+ lea Counter,a0 addq.l #1,(a0) move.l (a0),(a1) movem.l (sp)+,a0-a1 move.l #$45202001,d0 ; Return value expected by the game rts Call_B_READ: jmp $80000000 Counter: dc.l 0
Nec PC-9801
Both 3.5 inch and 5.25 inch floppy disks of Dungeon Master and Chaos Strikes Back use exactly the same format that is used on the X68000 versions (see above), including the same special copy protection features found on track 1 (on both sides).
- Dungeon Master for PC-9801 version 2.0a
- The copy protection is very similar to the X68000 version: the same two copy protection schemes are enabled and all the others are disabled.
The copy protection scheme that reads sector 9 twice to find random bytes is used when identifying the game disk, just like in the X68000 version.
The copy protection scheme that is broken in the X68000 versions is operational in this version. From time to time, and depending on the player’s activity, this protection reads the sector 9 random bytes and later analyzes these readings to make sure randomness is found. When a copy is identified, one of two consequences is triggered but not immediately: ‘SYSTEM ERROR 60’ is displayed and the game is stopped, or new events cannot be created anymore (inability to open doors, to perform actions with weapons or cast spells, etc.). - Dungeon Master for PC-9801 version 2.0b
- This version is not copy protected. All copy protection schemes are present but disabled in the program. The floppy disk still has the copy protection features on track 1 on both sides.
- Chaos Strikes Back for PC-9801 version 3.1
- The copy protection scheme in this version is unique compared to all other versions. The Chaos Strikes Back for PC-9801 floppy disk has the following differences compared to the Dungeon Master for PC-9801 floppy disk:
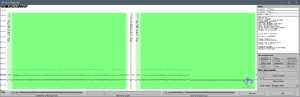
- An additional fake sector 240 with a wrong CRC and no data is located in the gap between sectors 3 and 4 of track 1 on side 0, as seen on this screenshot where the red band in the center is for T (track) 1, H (head = side) 0, S (sector) 240:
- Sector 9 on track 1 side 1 contains the string ‘015-000’ (7 characters) instead of ‘HPR-0007’ (8 characters). This string is still followed by 4 random bytes. Check this screenshot:
- Data in gaps: the gap located after sector 1 in track 0, side 0 (which contains the boot sector) starts with two special bytes (they should be $4E bytes but are not). The gaps located after sectors 1 to 5 on track 2, side 0 (which contain parts of the system file MEGDOS.SYS) also start with 2 special bytes and even 7 special bytes in the case of sector 2.
There are copy protection checks only when the game starts (new game or load a saved game) and when saving the game: it reads data in ‘diagnostic mode’ on side 0 in either track 0 or 2 starting at sector 1 in order to read more data than the regular sector data, including bytes located in gaps. It computes a checksum of the resulting data and performs comparisons to make sure the special bytes in gaps have their expected values. It also checks that sector 240 exists on track 1 side 1 but cannot be read (no content). If one of these copy protection check fails, the game immediately requests insertion of the original game disk. There are no delayed consequences.
- An additional fake sector 240 with a wrong CRC and no data is located in the gap between sectors 3 and 4 of track 1 on side 0, as seen on this screenshot where the red band in the center is for T (track) 1, H (head = side) 0, S (sector) 240:
The copy protection of PC-9801 versions also has a major weakness: there are no checksums on the game code. Modifying the program to bypass the copy protection checks has no consequence so that cracking the game was fairly easy, much more than with Atari ST/Amiga/Apple IIGS versions.
Fujitsu FM-Towns
The FM-Towns versions were the only ones released on CD-ROM.
The copy protection is very basic: when the game starts, it checks that the Compact Disc has the correct number of audio tracks: 19 for Dungeon Master / 30 for Chaos Strikes Back. If the number of tracks is not correct then the game stops processing events which makes it unplayable: thrown items remain in the air, doors do not open/close anymore, etc.
Apart from the simple check described above, all other copy protection related code and variables are not present.
IBM PC
Dungeon Master for PC is not copy protected and uses the standard formats for both 5.25 inch and 3.5 inch floppy disks. All copy protection related code and variables are not present.
Nintendo SNES
Dungeon Master for SNES is not copy protected. Dumping and duplicating the cartridge ROM data is not enough because it also contains a unique and proprietary chip named DSP-2 used for some graphics processing. Modern emulators can run the game from a ROM image because they also emulate this processor.
Hacking
Crack the game
Cracked versions of Dungeon Master and Chaos Strikes Back are available for download on the page of each game version. Cracking instructions are also provided where available.
Trigger the copy protection
You may try the following actions with a copied disk to trigger some copy protection checks and their consequences (this list is not exhaustive):
- Start a new game / load a saved game
- Save the game
- Move between levels. Check for short floppy disk accesses when you do so as this usually cause reading of the copy protection sector. Then use the second action of any item in hand or cast a spell. This triggers analysis of the sector that was read. Repeat this process several times.
Copy an original disk
If you copy an original copy protected floppy disk of Dungeon Master or Chaos Strikes Back using your favorite disk copier, the copy will not have the fuzzy bits but normal bits instead. The game can easily detect their presence by reading them several times: if it gets random results, then it assumes the disk is original. If it gets consistent results, it assumes the disk is a copy.
The only way to make perfect copies is to use special hardware like:
- A Tracer disk duplicator machine similar to the ones that were used to produce the original disks. The problem is that this is VERY expensive hardware, so you’d better buy an original game!
- A Discovery Cartridge, which is a hardware add-on for the Atari ST with its accompanying software. It contains an advanced floppy disk controller that allows full control over the disk writing process. If you have this piece of hardware, you can make a perfect and working copy of an original Dungeon Master or Chaos Strikes Back for Atari ST floppy disk by using the following specifications for the tool:
[Credits: Jean Louis-Guérin (DrCoolZic)]DUNGEON MASTER by FTL GAMES/SOFTWARE HEAVEN INC. ! 0 : W 1 9 535 14 1 : R 10 R : 79 )
The first command “0 : W 1 9 535 14” instructs to read a portion of track “0” directly as flux transition spacings. In this track, “9” sectors are expected to have a good checksum. Synchronization type “1” means that the equivalent of “535” MFM bytes should be read as flux transition spacings starting after the “14"th set of 3 sync marks ($A1). The 14th set of sync marks is the one indicating the start of the data field of sector #7 which contains the fuzzy bits.
The second command “1 : R 10” instructs to read track 1 as an unprotected track containing 10 sectors
The third command “R : 79” instructs to repeat the previous command through track 79.
Reference documentation for Discovery Cartridge syntax - One of the modern and special floppy disk controllers may be used to make perfect disk images of any floppy disk, at the flux level.
These tools should also be able to write these images back onto a floppy disk (not tested) and duplicate the fuzzy bits, avoiding the need for any crack. Some examples:- Kryoflux: a device that can read and write raw images of any floppy disk. Note that Software Preservation Society (SPS, ex CAPS) has not yet released any IPF images of Dungeon Master and Chaos Strikes Back, except for version 3.6 that is not copy protected.
- Applesauce: for Apple IIGS versions. See also here
- Greaseweazle
- SuperCard Pro
History of this document
- Version 2.0 - January 10, 2021
- Added content for all platforms in addition to Atari ST/Amiga. Restructured content.
- Version 1.4 - July 8, 2015
- Added message posted by Doug Bell
- Version 1.3 - January 29, 2009
- Replaced the term “weak bits” by “fuzzy bits”. Corrected the short explanation of what they are and added a link to the page containing a detailed description. Added instructions to copy the game with a Discovery Cartridge.
- Version 1.2 - December 18, 2006
- Added links to the patent of the copy protection.
- Version 1.1 - May 8, 2004
- Added links to download the cracked versions of Dungeon Master for Atari ST v1.2 and Chaos Strikes Back for Amiga v3.3 as well as the assembler source code of Chaos Strikes Back for Atari ST version 2.1, all done by Meynaf. Many thanks Philippe Guichardon (Meynaf) for his fantastic job and useful information.
- Version 1.0 - February 15, 2004
- First release. Many thanks to Kieron Wilkinson from the CAPS Project for his help.